Inside the Chain: Designing Blockchain Challenges for Nextrace CTF
Nov 6, 2025
10 min read
Introduction
The Nextrace CTF brings together cybersecurity enthusiasts and blockchain hackers from around the world to solve real-world security puzzles. As one of the challenge authors, my goal was to design tasks that went beyond simple reentrancy exploits — challenges that truly capture the complexity and creativity of Web3 vulnerabilities.
In this article, I’ll walk you through the design process behind my four blockchain challenges — Function Caller, IPFS Pointer, Keystore Hunter, and Sepolia Sleuth — and share the ideas, lessons, and technical inspirations behind each one.
The Vision Behind the Challenges
Each challenge in the blockchain category was designed with a specific educational goal in mind — to illustrate key Web3 concepts and help players build a deeper understanding of how decentralized systems actually work. From smart contract logic and off-chain storage to key management and blockchain analysis, every task was meant to represent a different layer of the Web3 ecosystem.
The idea was simple — learn by doing. Through interactive problem-solving, players could explore how blockchain components interact, how data flows on-chain and off-chain, and how core principles like transparency and trust are implemented in practice.
Challenge Repository
All the blockchain challenges featured in this post are available on GitHub:
🔗 Repository: https://github.com/Rayane-Boucheraine/NexTrace-CTF-Blockchain-Challenges
🔑 Keystore Hunter
Overview
In this challenge, players are given a secret-phase.txt file containing a 12-word mnemonic phrase.
The goal is to import this mnemonic into MetaMask to restore the associated wallet, explore its accounts, and identify which account name (label) contains the flag.
Writeup
Open MetaMask in your browser (install it if you haven’t).
Click Import wallet → Import using secret recovery phrase.
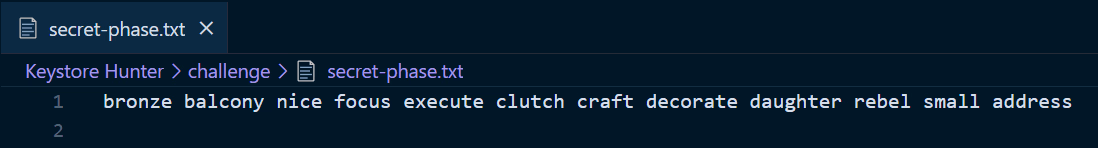
Copy the 12-word phrase from
secret-phase.txtand paste it into the input field.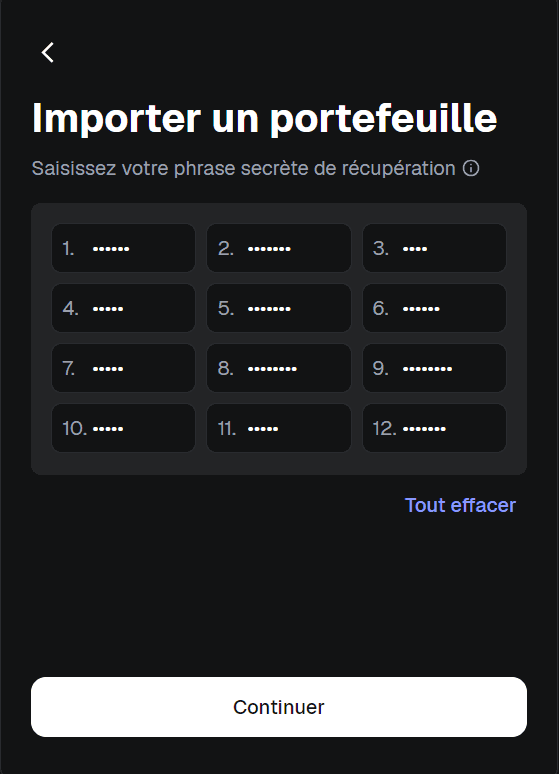
Set a strong password to secure your local MetaMask session.
Once the wallet is imported, open the account list — you’ll see multiple accounts derived from the same mnemonic.
One of these accounts has a name (label) that contains the flag.
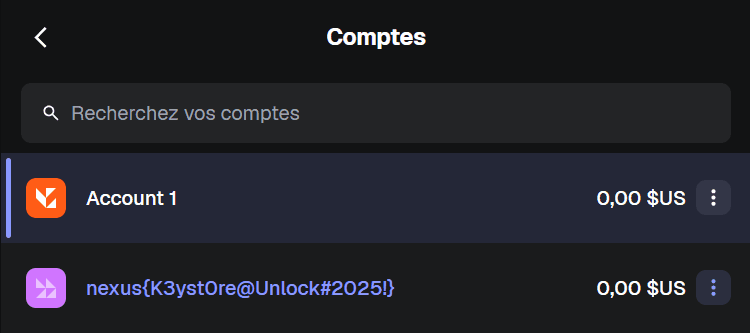
✅ That account name is your flag: nexus{K3yst0re@Unlock#2025!}
🔎 Sepolia Sleuth
Overview
This challenge teaches a core Web3 concept: the blockchain is transparent. The task is simple — given a Sepolia transaction hash, inspect the transaction and extract the flag embedded in its input data.
Writeup
Take the provided transaction hash:0x30ec55c058e4547bdb411489ea40e56d2331cd1a1ecd756a45c932e11650fa91
Open Sepolia Etherscan:
https://sepolia.etherscan.ioPaste the transaction hash into the search bar and open the transaction page.
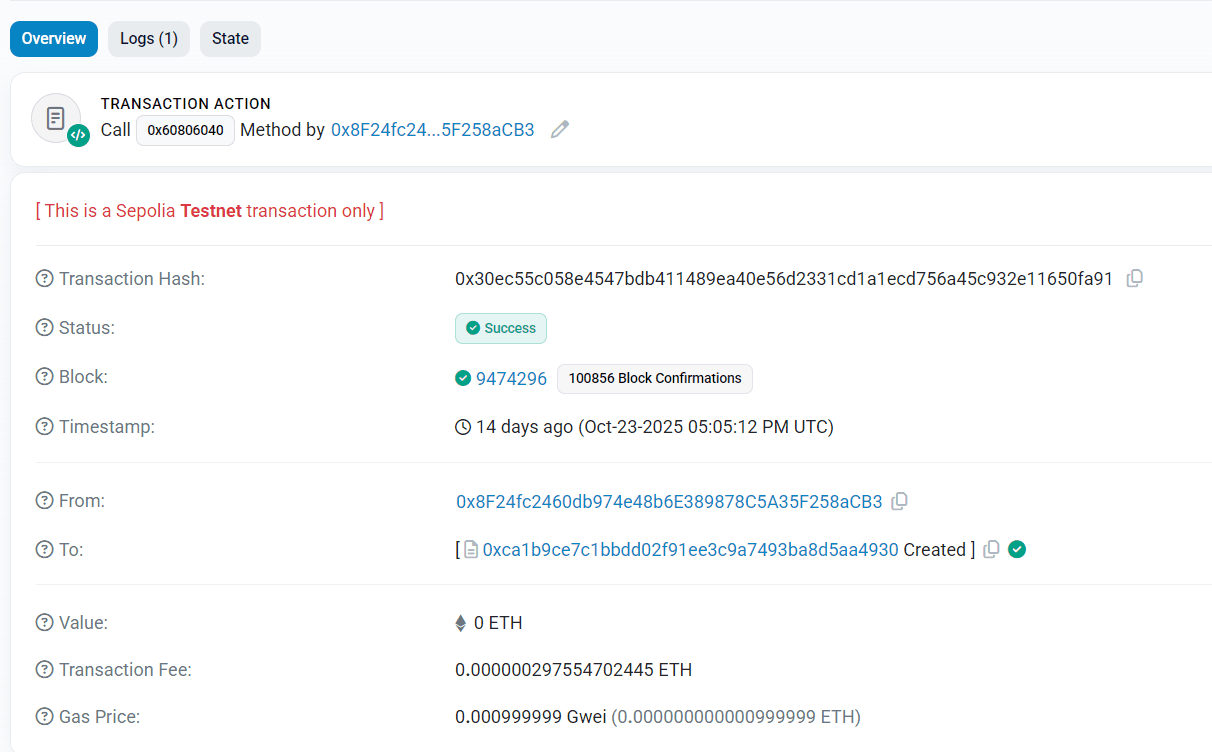
Scroll to the Input Data section.
Click View Input As: UTF-8 to decode the hex payload into readable text.
Search the decoded text for
nexus{and you will find the flag.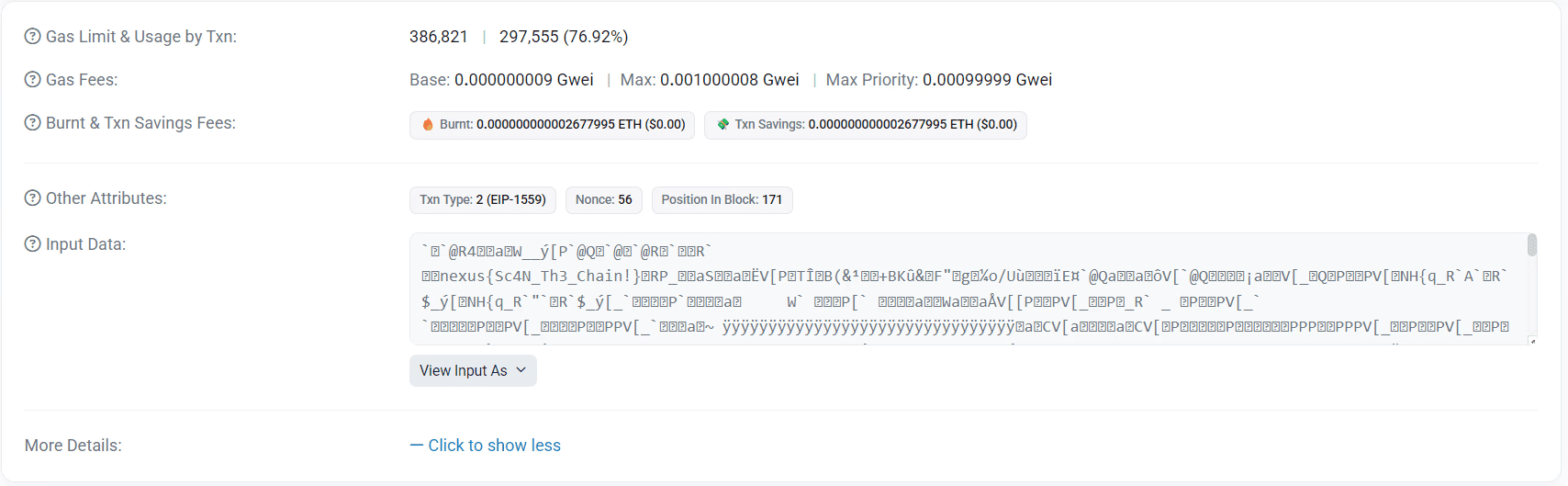
✅ The flag: nexus{Sc4N_Th3_Chain!}
🌐 IPFS Pointer
Overview
Players are given a smart contract address on the Sepolia testnet. The contract doesn’t store the flag directly — it stores an IPFS CID (a pointer). The task is to read that CID from the contract, fetch the off-chain file via an IPFS gateway, and extract the flag inside.
Writeup
Open the contract page on Sepolia Etherscan:https://sepolia.etherscan.io/address/0x92d2193f671eaeeb4b8cd4a9813fb4194ca0cbbd
Go to the Read Contract tab.
Look for a public variable namedcid(public variables expose a getter).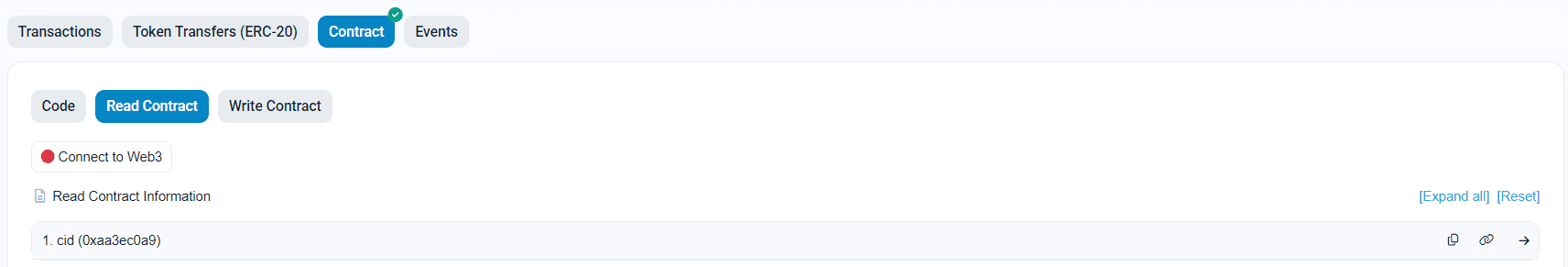
Click Query on
cid()— the contract will return an IPFS CID: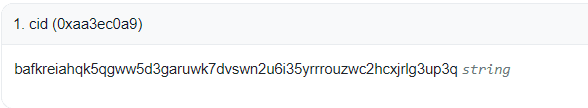
Open the CID in an IPFS gateway in your browser:
https://ipfs.io/ipfs/bafkreiahqk5qgww5d3garuwk7dvswn2u6i35yrrrouzwc2hcxjrlg3up3qThe retrieved file will contain the flag. 🎯
✅ The flag: nexus{L3aRn1ng_bL0ckChAi1n_w1tH_IpFs}
Overview
This challenge introduces players to the concept of hidden functions in unverified smart contracts.
On the Sepolia testnet, a contract was deployed without verified source code — meaning players must analyze its bytecode to find which functions actually exist.
The goal is to identify and call the hidden function that returns the flag.
Writeup
Go to the contract on Sepolia Etherscan:
https://sepolia.etherscan.io/address/0x33e120170FB87ef11716e281449780abB9DaC050Open the Contract tab.
You’ll notice that the source code might not reveal all the functions.
This means some were either not published or obfuscated at compile time.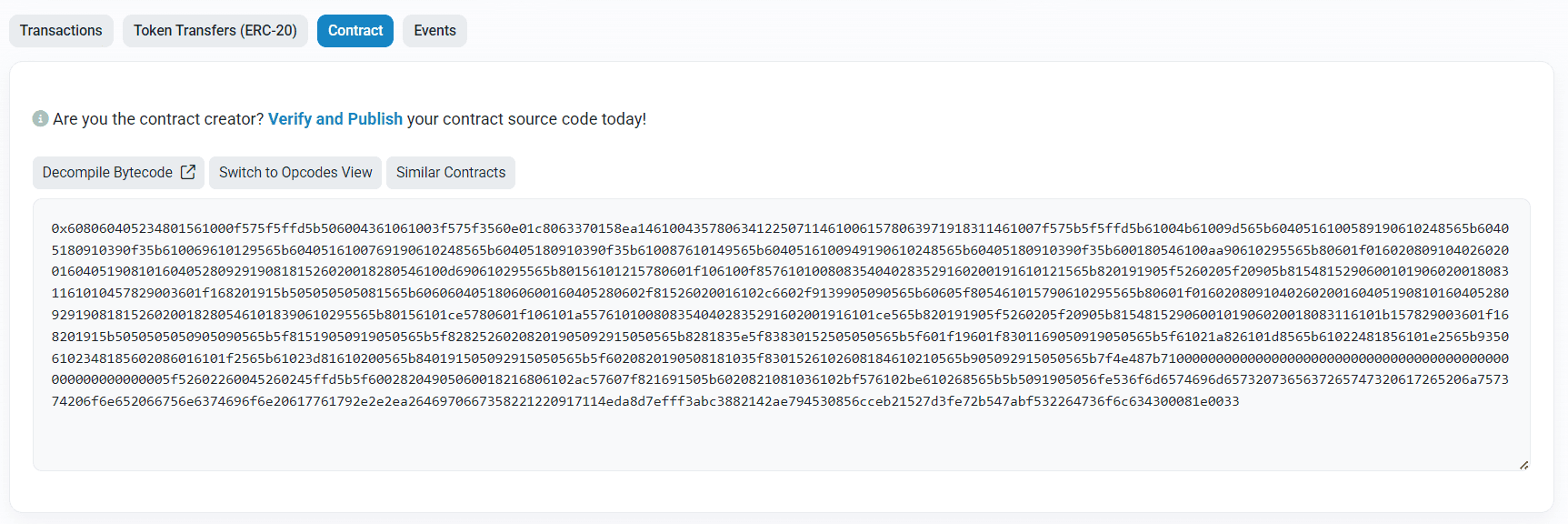
Switch to Bytecode → Opcodes view.
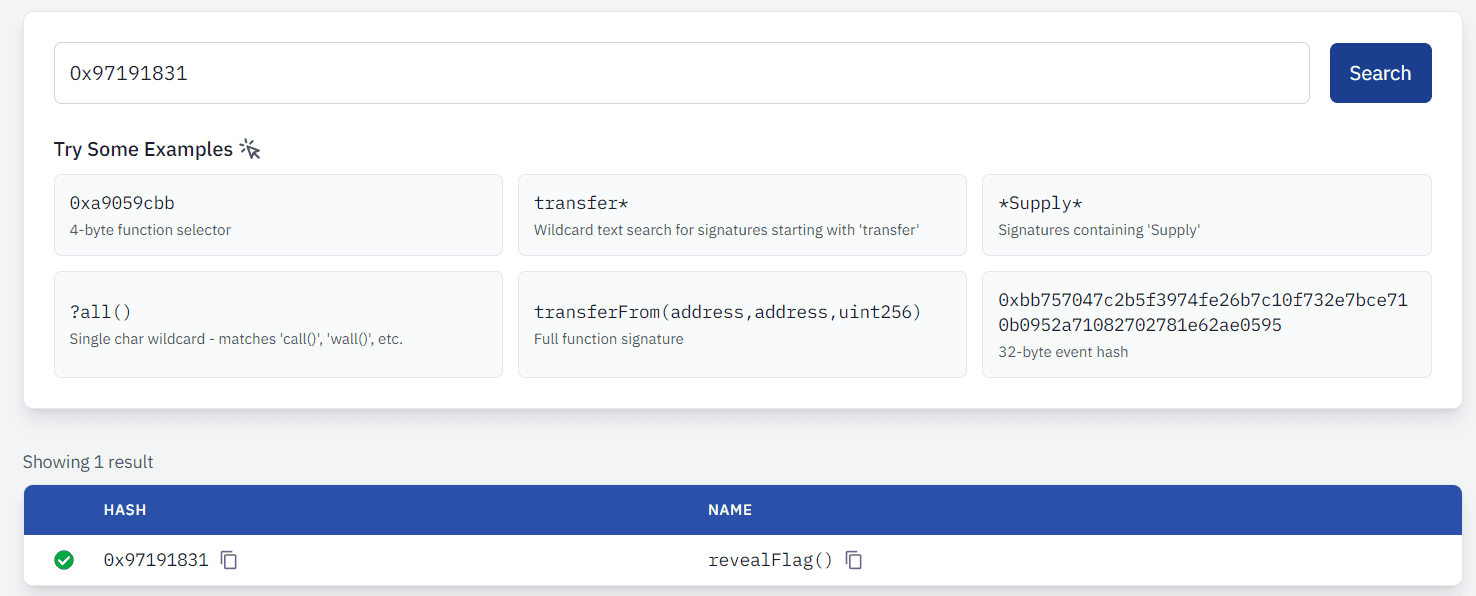
Search the opcodes for
PUSH4instructions.Each
PUSH4contains a 4-byte function selector.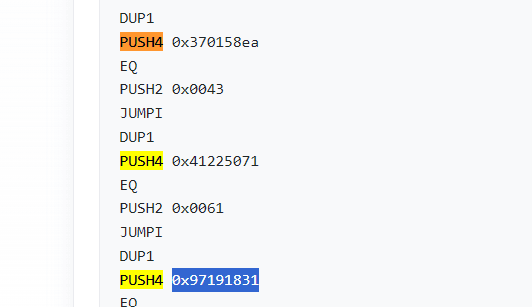
Copy the
PUSH4selectors you find.Decode selectors to possible function names using signature lookup sites:
Prepare to call the function(s):
RPC URL (Sepolia):
https://sepolia.infura.io/v3/9aea22bcb5aa48a095a163d66533301eOptions to call:
cast(Foundry), orethers.js.
Now you have a decoded name, call it directly.
Example withcast:cast call 0x33e120170FB87ef11716e281449780abB9DaC050 "revealFlag()" --rpc-url https://sepolia.infura.io/v3/9aea22bcb5aa48a095a163d66533301eObserve the call result — one of the functions will return the flag directly on-chain.
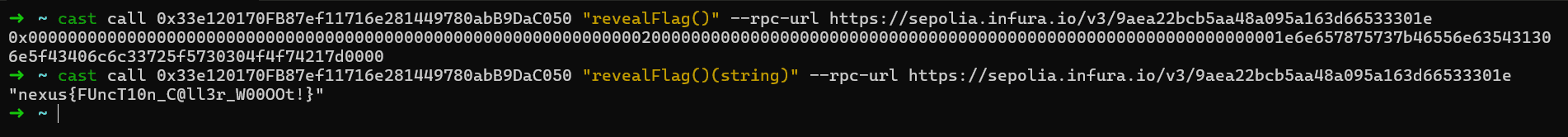
✅ The flag: nexus{FUncT10n_C@ll3r_W00OOt!}